In this blog post, we are going to discuss one of the interesting findings of Nirmal Dahal, Head of Security at CryptoGen Nepal Pvt. Ltd. on the website of Samy Kamkar (https://en.wikipedia.org/wiki/Samy_Kamkar). Before jumping into the technical details, let’s discuss the target of the attack. Samy is an American privacy and security researcher, computer hacker, entrepreneur and a big influencer for many InfoSec members. Samy Kamkar is the person who created the first JavaScript-based worm known as Samy Worm which went viral within a few hours ultimately compelling myspace to shut down temporarily.
While he was explaining the work of Samy Kamkar to one of our co-workers, he happened to stumble upon Samy’s website. The site has so many Easter-eggs like challenges. Visitors of the site are not allowed to view the source code using normal methods like ‘right-click’, ‘Inspect element’, ‘Ctrl + shift + I’ etc. After trying the following snippet.
javascript:https://samy.pl/?%0aalert(document.body.innerText=document.body.innerHTML)
He was able to see the source code that was extracted from the DOM for the Samy’s website.
You can go to https://samy.pl and try to right-click, view his source code using CTRL + U or even go to another tab and type:
view-source:https://samy.pl
Lastly, try to view the source using the inspect element and comment if you find anything interesting. Please reply if you find any other way to view the source code.
After exploring through resources on the website, Mr. Dahal saw that he was using JS code to detect proxies like Burp, Charles & Fiddler. Finding it interesting, Mr. Dahal dug deeper to see everything Samy was using to make the website as interesting as it was. This search leads to a suspicious “jsonp endpoint” that was used to reflect the public IP address of whoever is requesting his website.
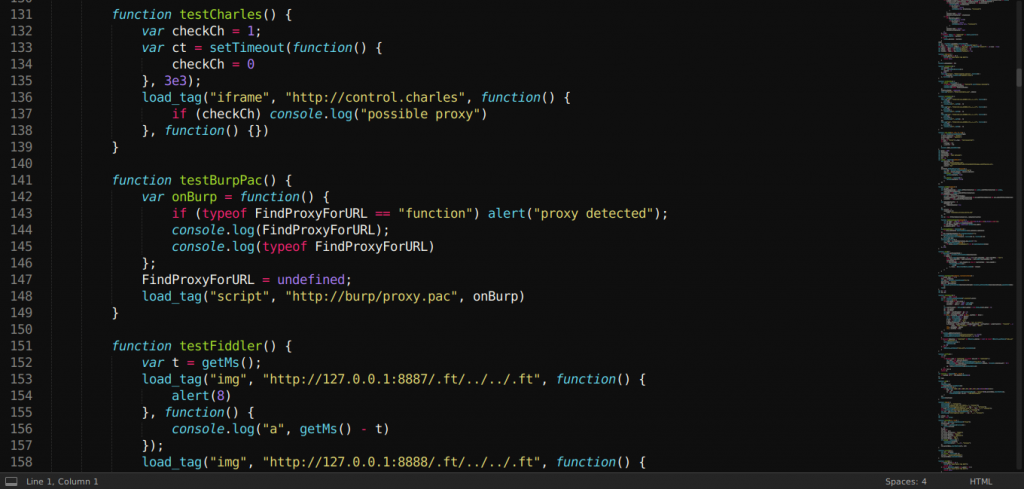
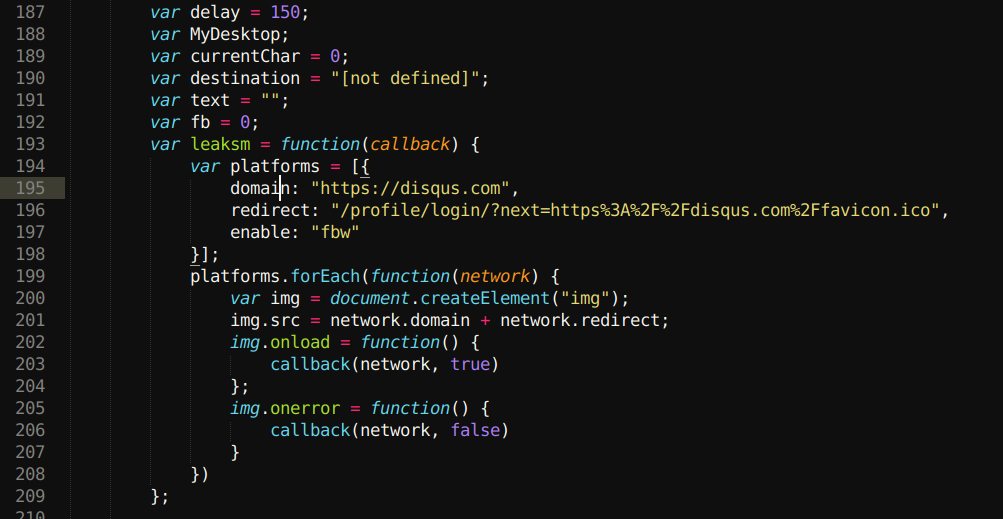
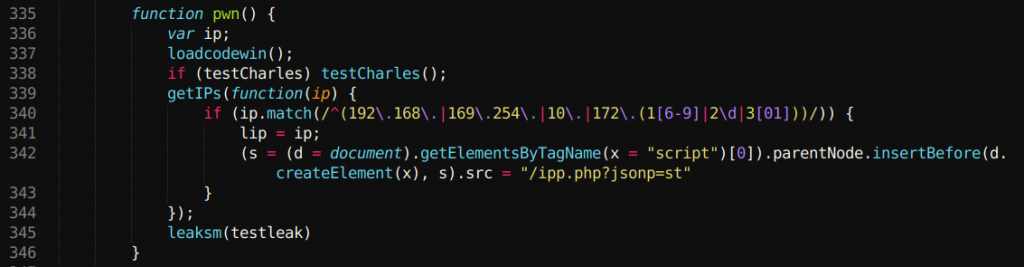
The endpoint was something like https://samy.pl/ipp.php?jsonp=st then it would reflect something like this
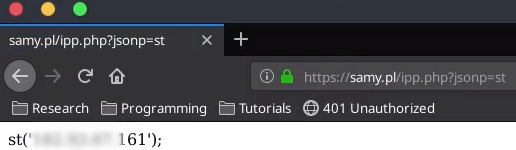
Upon viewing the endpoint he started to alter the endpoint. Removing ‘st’ from the endpoint also removed it from the reflected output.
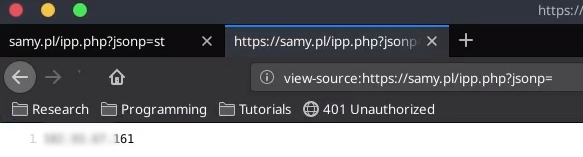
Mr. Dahal continued to alter the endpoint and added ‘<>’ which was successfully reflected on the site.
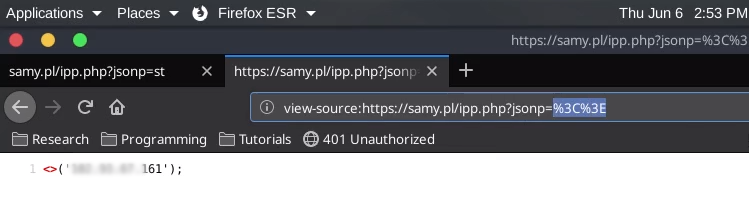
The output made him realize the endpoint was vulnerable to XSS and used one of his custom scripts to reflect a cross-site scripting vulnerability that was successfully executed.
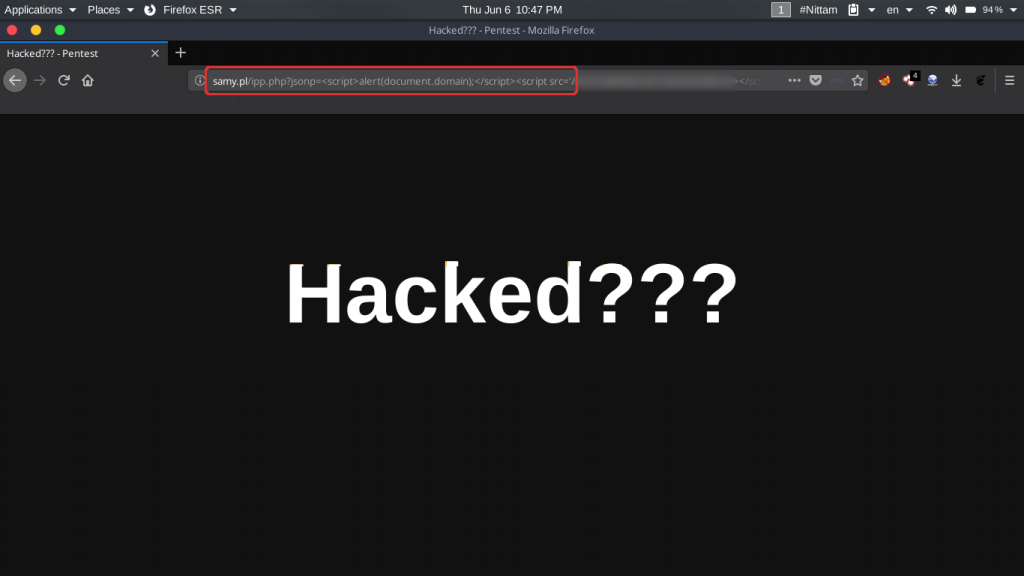
Video PoC :
Timeline :
- June 6, 2019 – Report Sent
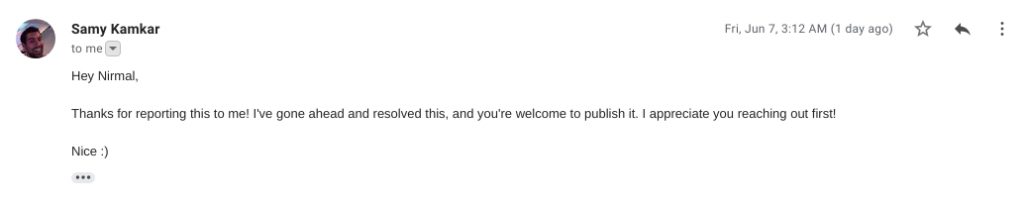
- June 7, 2019 – Fixed & allowed to publish by Samy Kamkar
Note: Finding an XSS issue in Samy Kamkar’s site, one of the first JavaScript-based worm creator, proves that no system can be 100% secure no matter how much experienced the owner/developer is. It is only a matter of time and the amount of knowledge to discover a new or even existing flaw.
धन्यवाद !!!




